Estimated reading time: 5 min
Enable Burp Suite proxy feature
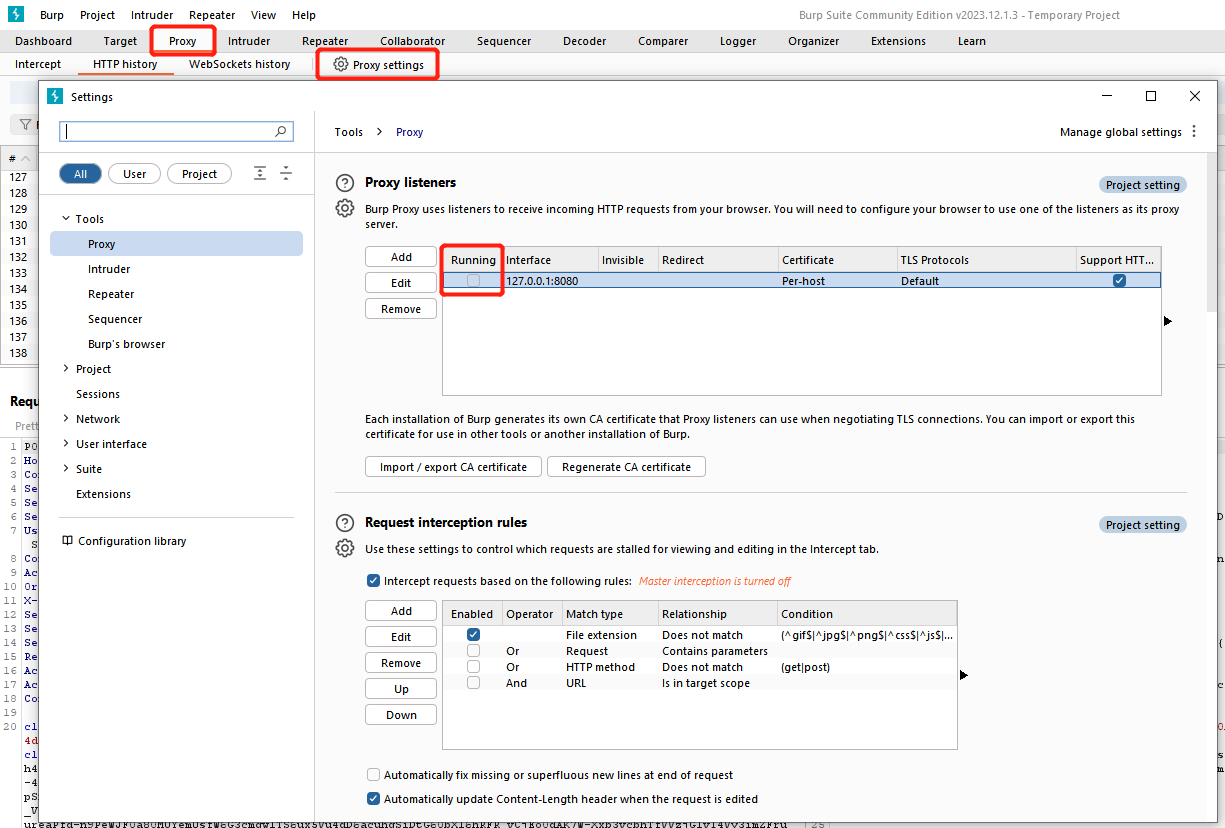
Open Burp Suite, select Proxy > Options menu.
In the Proxy Listen Address textbox, enter the local IP address and port number, default 127.0.0.1:8080.
In the pop-up window, ensure the Running option is enabled (green check).
Configure Windows proxy settings
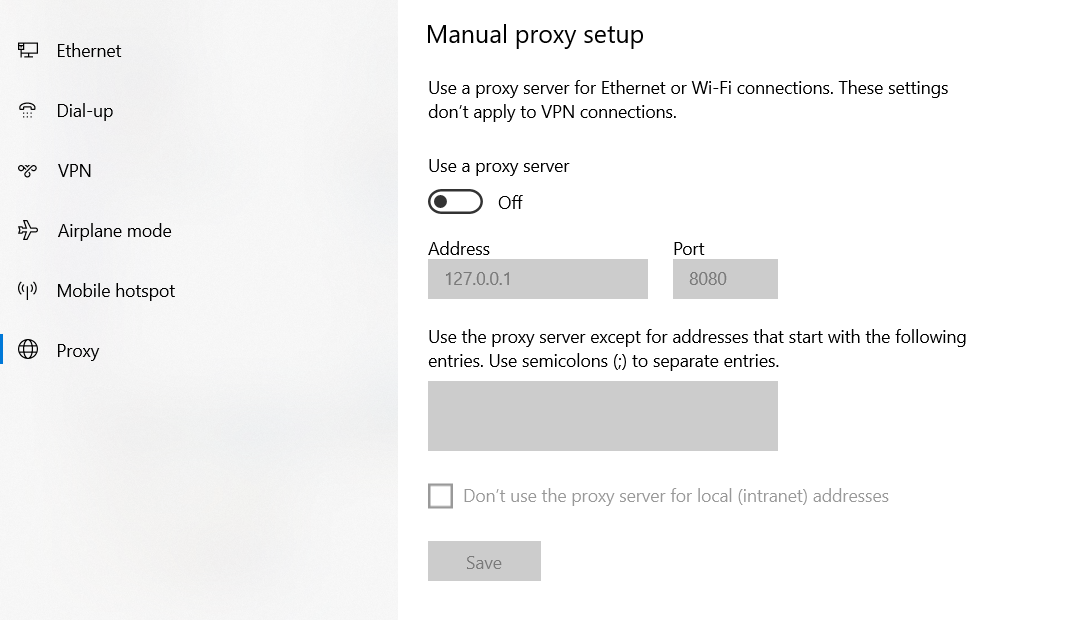
Set up proxy in the network settings of your machine, proxy address 127.0.0.1, proxy port 8080.
Fill in and Save to apply.
Install Burp Suite certificate
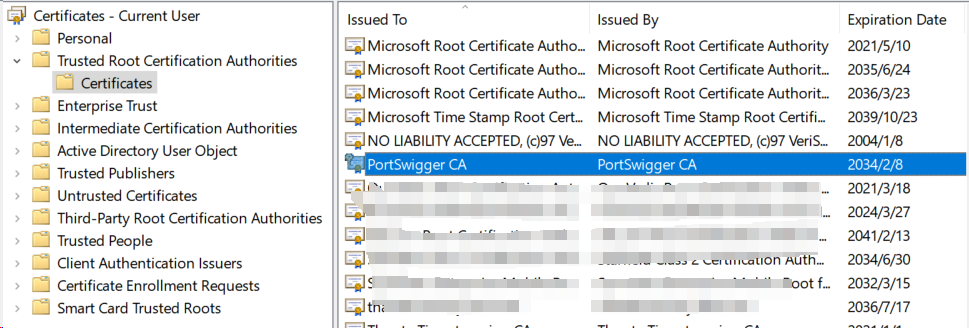
Use a browser to open http://burp, click on the top right corner to download and install the Burp Suite certificate.
It is recommended to install it for the local machine; installing for the current user only might still prompt that the certificate is untrusted.
After installation, use certmgr to check that there is a PortSwigger certificate under Trusted Root Certification Authorities, which means the installation was successful.
Test HTTPS packet capture
Visit an HTTPS website in your browser, such as https://www.google.com. In Burp Suite's Proxy tab under HTTP history, you should be able to see all requests and responses.
This method can parse HTTPS requests from browsers and other applications for analysis and troubleshooting.
Since Burp Suite captures all HTTPS requests, if targeting a specific application, you can use the Proc Mon tool to view the application's requests, and use Burp Suite to filter the application's requests accordingly.
Can Burp Suite's functionality intercept HTTPS requests from specific applications only? (to be continued)
Using Wireshark with Windows Environment Variables to Capture HTTPS Data Analysis
Windows Environment Variable Configuration
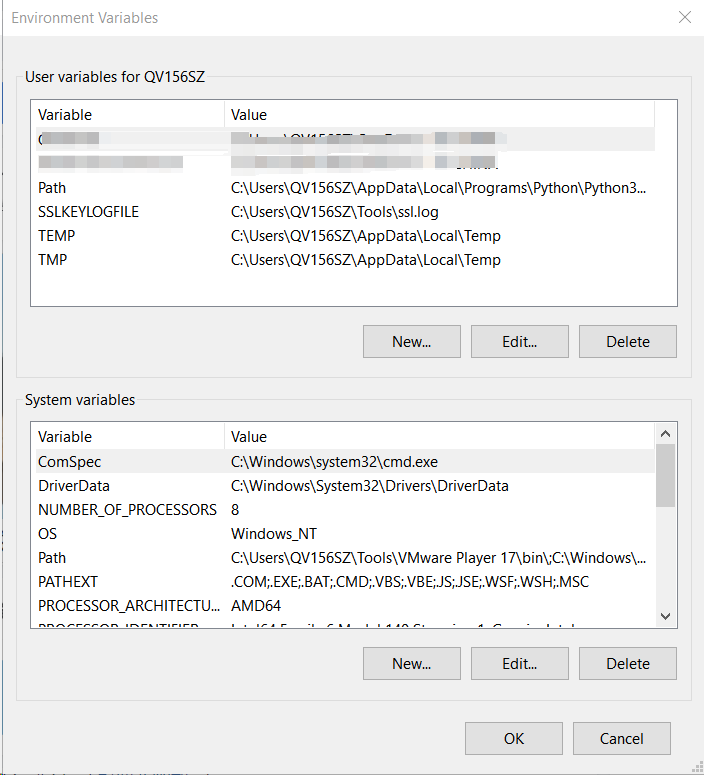
In System Properties > Advanced > Environment Variables, you can add as either a User or System.
Add an environment variable:
Variable: SSLKEYLOGFILE
Value: C:\the\path\to\SSLkey.log
Configure Wireshark options
Open Wireshark and select Edit > Preferences > Protocols > TLS, in the (pre)-master-secret log filename choose the set file C:\the\path\to\SSLkey.log.
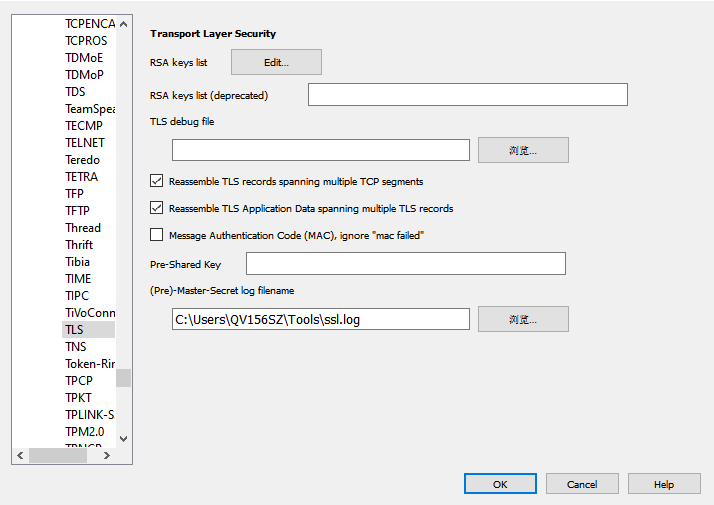
Test HTTPS packet capture
After starting the capture, Wireshark will use the handshake information saved in this file, then it can parse out the browser's HTTPS requests (it seems other applications won't save here), for analysis and troubleshooting.
When the capture is completed, save this file as another file, together with the capture file, so you can import this file later to parse the HTTPS requests of this capture.
Note:
The SSLKEYLOGFILE is saved in plain text, so security measures are needed. This file will continue to be written to due to the environment variable, so it needs to be cleaned regularly or the environment variable should be deleted after use.

